Resource / Online Journal
What is The Cyber Kill Chain and How to Use it Effectively
Discover how the Cyber Kill Chain model helps organizations identify, disrupt, and prevent cyberattacks. Learn how combining it with modern tools enhances your cybersecurity defenses.
Published on Mar 17, 2025

Cyber Kill Chain Explained
The Cyber Kill Chain/ Cyberattack Chain is a cybersecurity framework designed to help security teams identify, interrupt, and prevent sophisticated cyberattacks before they cause harm to an organization. By breaking down an attack into distinct stages, this model provides insight into how cyber threats unfold and where defenders can take action to mitigate risks.
As a strategic framework that aids businesses in effectively identifying, responding to, and mitigating cyber-attacks, the Cyber Kill Chain is still essential in today's cybersecurity environment. Businesses can create an effective security posture by implementing this strategy, which will make it much more challenging for attackers to succeed.
Understanding the Cyber Kill Chain Model
The Cyber Kill Chain, first introduced by Lockheed Martin in 2011, is a framework that helps cybersecurity teams detect, disrupt, and prevent sophisticated attacks before they cause damage. Cyberattacks occur in stages, making it possible to identify and neutralize threats before they escalate. This framework is particularly useful in defending against Advanced Persistent Threats (APTs)—attacks where adversaries invest time in planning and executing stealthy cyber intrusions.
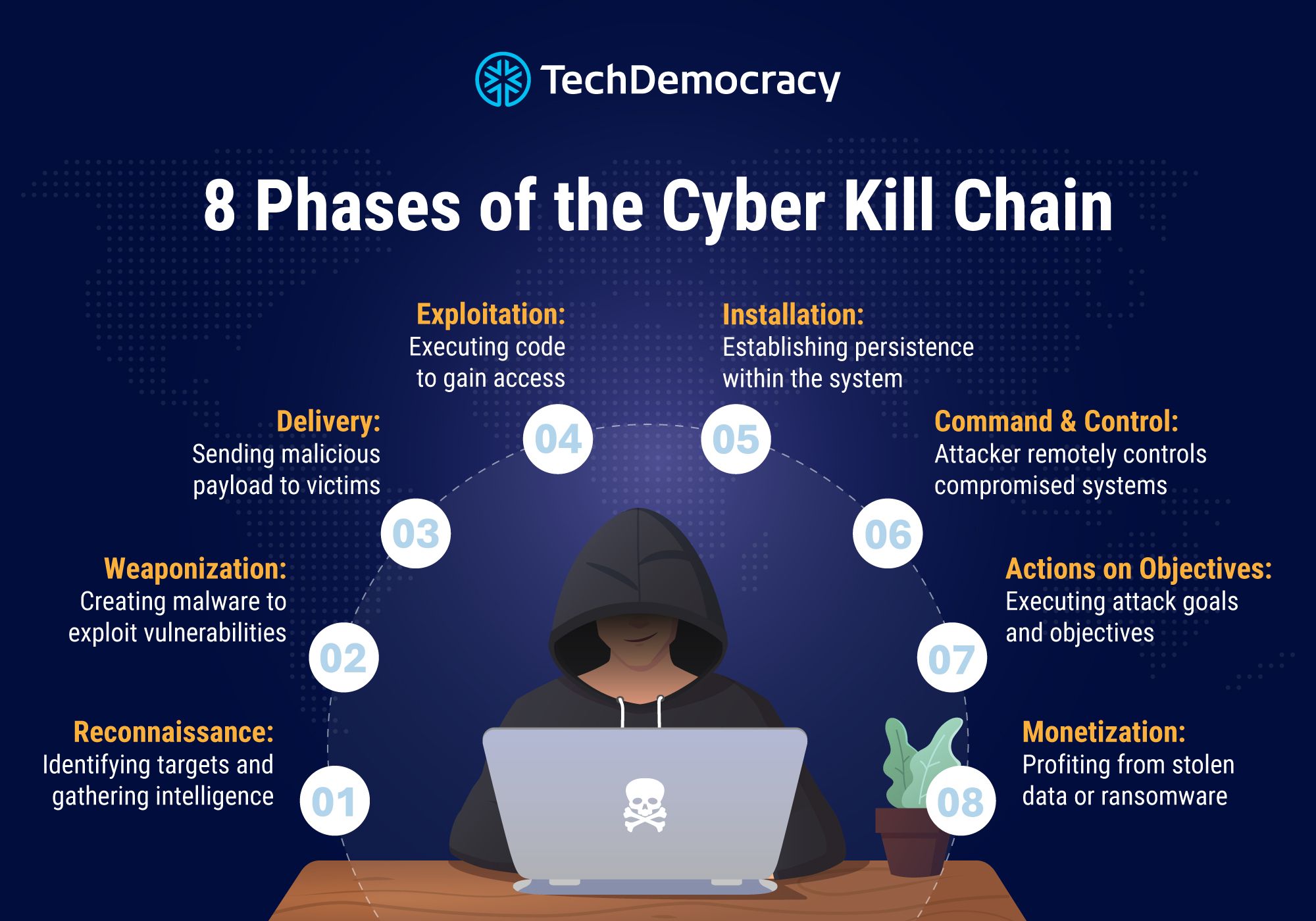
8 Phases of the Cyber Kill Chain & How it Works
The Cyber Kill Chain is Originally designed with seven phases, the Cyber Kill Chain has since evolved as cyber threats have become more sophisticated. Cybersecurity experts introduced an eighth phase—Monetization—to highlight the financial motives behind attacks, such as ransomware demands, selling stolen data, and financial fraud.
How the Cyber Kill Chain Works
1. Initial Reconnaissance:
In the initial phase, cybercriminals study their target, they gather intel on weaknesses, employee credentials, and system vulnerabilities. This phase involves:
- Scanning public websites, social media, or leaked credentials.
- Harvesting login credentials and user details.
- Identifying weak network configurations and exposed systems.
2. Weaponization:
In this phase, the malicious actor may work on a custom-made virus to ransomware designed to exploit a specific vulnerability. Techniques include:
Developing ransomware, viruses, trojans, or worms.
Embedding malware in seemingly harmless files.
Creating backdoors for persistent access.
3. Delivery:
Attackers find ways to deliver their malicious payload, often using deception. Common methods include:
Phishing emails with infected attachments or links.
Drive-by downloads from compromised websites.
Exploiting unsecured public Wi-Fi networks.
4. Exploitation:
Once inside, the attacker exploits the system vulnerabilities to gain control. Some of the most common tactics are:
Privilege escalation to gain administrative control.
Running malicious scripts or altering security settings.
Exploiting zero-day vulnerabilities in software.
5. Installation:
To stay in the system long-term, the attacker installs malware or backdoors, ensuring they can return even if detected. Key activities include:
- Installing Remote Access Trojans (RATs).
- Embedding keyloggers to steal credentials.
- Setting up backdoors to ensure continued access.
6. Command and Control:
With a firm grip on the system, attackers establish remote control. They may move undetected across networks while masking their activity. This stage involves:
- Connecting the infected system to malicious command servers.
- Using obfuscation techniques to hide activity.
- Deploying denial-of-service (DoS) attacks to distract security teams.
7. Actions on Objectives:
Now that they have control, attackers execute their mission—whether it’s stealing sensitive data, encrypting files for ransom, or disrupting business operations. Their goals could include:
- Stealing sensitive data (e.g., personal information, trade secrets).
- Encrypting files and demanding ransom (ransomware attacks).
- Disrupting operations through data corruption or system shutdowns.
8. Monetization:
Once they’ve completed their objective, they turn their efforts into profit through:
- Demanding ransom payments from victims.
- Selling stolen data on the dark web.
- Using compromised financial data for fraudulent transactions.
Role of threat intelligence and perimeter security
The Cyber Kill Chain approach has been criticized for its over-reliance on malware prevention and perimeter security. Despite being the cornerstones of cybersecurity, these are losing their effectiveness as businesses embrace remote work, embrace IoT, and move from traditional on-premises networks to cloud settings. Robotic process automation (RPA), third-party interfaces, and the increasing usage of personal devices have all greatly increased the attack surface, making it more difficult for businesses to defend every possible point of access.
Cybercriminals are becoming increasingly sophisticated, using advanced tactics to exploit both software and hardware vulnerabilities. Common attacks, such as phishing emails, misconfigured firewalls, and supply chain breaches, highlight the limitations of perimeter-based security. While perimeter security is designed to block external threats, it can benefit from analyzing past attacks through the Cyber Kill Chain model, allowing organizations to identify attack patterns, understand adversary tactics, and adjust defenses accordingly.
By integrating perimeter security with threat intelligence, organizations can create a more robust cybersecurity strategy. Perimeter security works to prevent initial intrusions, while threat intelligence helps businesses stay ahead of attackers by continuously adapting to emerging threats. Combining these approaches enables organizations to minimize security gaps and strengthen overall resilience.
Enhancing Cybersecurity with the Cyber Kill Chain Framework
The Cyber Kill Chain enhances cybersecurity by enabling early attack detection and prevention. The Reconnaissance and Weaponization stages allow for early disruption, and integrating threat intelligence helps identify attack patterns and adversary tactics, blocking attacks before they succeed.
By securing multiple layers of the network—such as using email filters to block phishing and applying patch management to close vulnerabilities—businesses can prevent attackers from progressing through the kill chain. These proactive defenses reduce the likelihood of successful attacks.
The Cyber Kill Chain’s adaptability is a key advantage. By integrating with modern security tools like IDS, firewalls, and endpoint protection, organizations can continuously strengthen their defenses, ensuring risks are mitigated throughout the entire attack lifecycle.
Integration with other frameworks like MITRE ATT&CK
The Cyber Kill Chain's effectiveness is significantly enhanced when integrated with other established frameworks, such as MITRE ATT&CK. By combining both, organizations gain a more granular and comprehensive understanding of the attack life cycle and the specific actions adversaries are likely to take at each stage.
Detailed Threat Detection:
The Cyber Kill Chain outlines the stages of an attack, while MITRE ATT&CK details the specific tactics and techniques attackers use at each stage. This allows organizations to identify not just the presence of an attack but also the specific methods used.
Improved Incident Response:
The Cyber Kill Chain provides an overarching view of attack progression, while MITRE ATT&CK breaks down adversary actions into detailed techniques. When combined, they refine incident response plans, enabling more proactive and precise responses at each stage of an attack.
Proactive Threat Hunting:
By integrating both frameworks, security teams can anticipate attacks by understanding the tactics, techniques, and procedures (TTPs) likely used by attackers. This proactive approach allows security teams to hunt for indicators of compromise (IOCs) before an attack escalates.
Comprehensive Risk Management:
The detailed insights from MITRE ATT&CK allow organizations to conduct thorough risk assessments, identifying the most vulnerable stages in their cybersecurity posture and applying targeted countermeasures.
Continuous Improvement and Adaptation:
Both frameworks allow for continuous updates, ensuring that organizations stay aligned with evolving threat intelligence. As new techniques are identified in MITRE ATT&CK, they can be mapped back to the Cyber Kill Chain, enhancing the organization’s defenses against emerging threats.
Insights on combating modern cyber threats
To combat modern cyber threats effectively, organizations must adopt a multi-layered, proactive approach to cybersecurity. This includes leveraging advanced technologies like Zero Trust, EDR, threat intelligence, and automated response, alongside fostering a culture of security awareness and continuous improvement. The evolving threat landscape demands that cybersecurity defenses evolve just as quickly, ensuring that businesses can adapt and stay resilient in the face of ever-changing cyber risks.
Importance of security awareness training and intrusion prevention systems
Humans are often the weakest link in an organization’s security posture. Security awareness training helps employees recognize threats like phishing, social engineering, and malicious tactics. Here’s why it’s crucial:
Reduces Human Error: Cyberattacks exploit human mistakes, such as clicking on phishing links or using weak passwords. Training employees to spot suspicious emails and follow security best practices reduces the chances insider threats.
Improves Detection and Response: Trained employees are more likely to detect and report security incidents quickly. They can identify phishing or malware infections early, allowing IT teams and security professionals to address issues before they escalate.
Cost-Effective Defense: Employee awareness training is a low-cost, high-impact investment. It builds a security-conscious culture and dramatically reduces the likelihood of a data breach, ultimately minimizing financial and reputational damage.
Conclusion
The Cyber Kill Chain model is a key framework for cybersecurity professionals, offering insights into how attacks unfold and where businesses can intervene. By understanding each stage, from reconnaissance to monetization, organizations can proactively neutralize threats early and reduce damage.
As cyber threats become more sophisticated, relying solely on perimeter defenses is no longer enough. Integrating the Cyber Kill Chain with advanced tools, threat intelligence, and frameworks like MITRE ATT&CK strengthens security against evolving adversaries.
Partnering with cybersecurity solution providers like TechDemocracy helps businesses stay ahead of emerging risks, future attacks, protecting systems, data, and reputation for the long term.
Recommended articles


Comprehensive Guide to Oracle Cloud Infrastructure Identity Access Management Concepts
Take Your Identity Strategy
to the Next Level
Strengthen your organization's digital identity for a secure and worry-free tomorrow. Kickstart the journey with a complimentary consultation to explore personalized solutions.